# Linux之利用Google Authenticator实现用户双因素认证(Red Hat Enterprise Linux 6.0)
2017.04.19
# 一、Google-Authenticator双因素认证
双因素身份认证就是通过你二个要素组合到一起进行身份认证系统,比如登陆时,不但要输入密码还需要输入动态验证码。Google-Authenticator双因素认证是一种采用时间同步技术的系统,采用了基于时间、事件和密钥三变量而产生的一次性密码来代替传统的静态密码。每个动态密码卡都有一个唯一的密钥,该密钥同时存放在服务器端,每次认证时动态密码卡与服务器分别根据同样的密钥,同样的随机参数(时间、事件)和同样的算法计算了认证的动态密码,从而确保密码的一致性,从而实现了用户的认证。 双因子身份认证机制的安全分析http://bobao.360.cn/learning/detail/2811.html
# 二、linux上的实现方式
linux登陆认证支持PAM模块(插入式验证模块 https://www.ibm.com/developerworks/cn/linux/l-pam/),将Google-Authenticator的模块配置到ssh登陆中。从而实现密码和手机动态口令的双因子认证
# 三、功能组件
手机端需要安装Google Authenticator , ios搜索安装,安卓可以从这里安装:酷安网 http://www.coolapk.com/apk/com.google.android.apps.authenticator2 google play, https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2
服务器端需要安装PAM Google Authenticator pam https://github.com/google/google-authenticator-libpam Google Authenticator https://github.com/google/google-authenticator
# 四、开始安装
1.首先,将源改为阿里云的源,并增加RepoForge源,
rpm -ivh http://repository.it4i.cz/mirrors/repoforge/redhat/el6/en/x86_64/rpmforge/RPMS/rpmforge-release-0.5.3-1.el6.rf.x86_64.rpm
提示:下载地址从这里找 http://repoforge.org/use/
2.依赖包安装
yum install wget gcc gcc-g++ make
yum install autoconf automake libtool
yum install pam-devel libpng-devel qrencode chrony
2
3
3.下载google-authenticator-libpam,并编译安装
wget https://github.com/google/google-authenticator-libpam/archive/1.03.zip
unzip google-authenticator-libpam-1.03.zip
cd google-authenticator-libpam-1.03
2
3
4.编译
./bootstrap.sh
./configure
make
2
3
5.安装
make install
注意rhel 6.0还需要执行
ln -sv /usr/local/lib/security/pam_google_authenticator.so /lib64/security/pam_google_authenticator.so
提示:如果不创建软连接,/var/log/secure会报:
sshd[14318]: PAM unable to dlopen(/lib64/security/pam_google_authenticator.so): /lib64/security/pam_google_authenticator.so: cannot open
shared object file: No such file or directory
2
3
4
5
6
7
8
# 五、配置
- 安装配置时间同步chrony
vim /etc/chrony.conf
server 0.cn.pool.ntp.org
server 1.cn.pool.ntp.org
server 2.cn.pool.ntp.org
server 3.cn.pool.ntp.org
/etc/init.d/chronyd restart
chronyc sources
2
3
4
5
6
7
8
- 修改pam配置文件
(1) 改变password-auth的软连接
cd /etc/pam.d
cp password-auth password-auth-google
cp password-auth password-auth-backup
rm password-auth
ln -sv password-auth-google password-auth
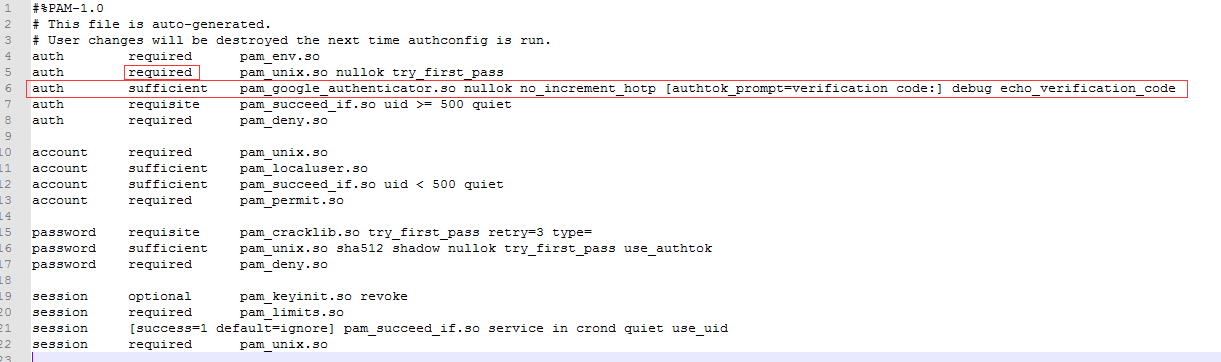
(2) 修改password-auth-google文件,
auth sufficient pam_unix.so nullok try_first_pass
修改为
auth required pam_unix.so nullok try_first_pass
auth sufficient pam_google_authenticator.so nullok no_increment_hotp [authtok_prompt=verification code:] debug echo_verification_code
2
3
4
5
6
7
8
9
10
11
如图:
- 修改ssh服务配置
vim /etc/ssh/sshd_config
PasswordAuthentication yes
ChallengeResponseAuthentication yes
UsePAM yes
2
3
4
- 禁用selinux,否则root用户无法登陆,会报
#下次重启生效
vi /etc/selinux/config
SELINUX=disabled
SELINUXTYPE=targeted
#立即生效
setenforce 0
2
3
4
5
6
7
- 同步时间
ntpdate 0.cn.pool.ntp.org
- 重启服务
service sshd restart
# 六、测试并登陆
- 新建用户test,并为test设置密码
- 第一次登陆,因为没有设置过google-authenticator, 所以会提示,配置google-authenticator
google-authenticator
Do you want authentication tokens to be time-based (y/n) y
你想做的认证令牌是基于时间的吗?
Warning: pasting the following URL into your browser exposes the OTP secret to Google:
https://www.google.com/chart?chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/root@localhost.localdomain%3Fsecret%3DN4HLEJOQHT27VCR6RX66WXB2SY%26issuer%3Dlocalhost.localdomain
[这里会有一个很大的二维码]
Your new secret key is: N4HLEJOQHT27VCR6RX66WXB2SY
这个key就是加密串,如果你有多个设备,需要把这个保存下,方便以后添加认证设备
Your verification code is 299695
输入手机上Google Authenticator的code
Your emergency scratch codes are:
下面这些key是紧急安全码,假如你的手机丢了,紧急登录用的。
44477086
92790948
29251218
26350870
30696065
Do you want me to update your "/home/test/.google_authenticator" file? (y/n) y
你希望我更新你的“/home/test/.google_authenticator”文件吗(y/n)?
Do you want to disallow multiple uses of the same authentication
token? This restricts you to one login about every 30s, but it increases
your chances to notice or even prevent man-in-the-middle attacks (y/n) y
你希望禁止多次使用同一个验证令牌吗?这限制你每次登录的时间大约是30秒, 但是这加大了发现或甚至防止中间人攻击的可能性(y/n)?
By default, a new token is generated every 30 seconds by the mobile app.
In order to compensate for possible time-skew between the client and the server,
we allow an extra token before and after the current time. This allows for a
time skew of up to 30 seconds between authentication server and client. If you
experience problems with poor time synchronization, you can increase the window
from its default size of 3 permitted codes (one previous code, the current
code, the next code) to 17 permitted codes (the 8 previous codes, the current
code, and the 8 next codes). This will permit for a time skew of up to 4 minutes
between client and server.
Do you want to do so? (y/n) y
默认情况下,令牌保持30秒有效;为了补偿客户机与服务器之间可能存在的时滞,
我们允许在当前时间前后有一个额外令牌。如果你在时间同步方面遇到了问题, 可以增加窗口从默认的3个可通过验证码增加到17个可通过验证码,
这将允许客户机与服务器之间的时差增加到4分钟。你希望这么做吗(y/n)?
If the computer that you are logging into is not hardened against brute-force
login attempts, you can enable rate-limiting for the authentication module.
By default, this limits attackers to no more than 3 login attempts every 30s.
Do you want to enable rate-limiting? (y/n) y
如果你登录的那台计算机没有经过固化,以防范运用蛮力的登录企图,可以对验证模块
启用尝试次数限制。默认情况下,这限制攻击者每30秒试图登录的次数只有3次。 你希望启用尝试次数限制吗(y/n)?
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
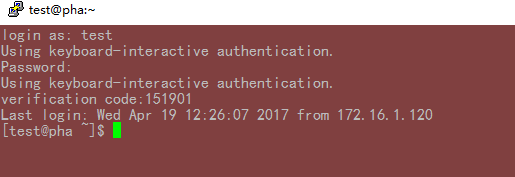
再次登陆,已经配置过google-authenticator,所以这次验证完密码,还需要验证动态验证码,如图
# 七、登陆问题查看日志
如果第一次登陆失败,
tail -n10 /var/log/secure
# 参考连接
https://www.antergone.com/60.html http://www.cnblogs.com/hanyifeng/p/kevin4real.html http://www.pool.ntp.org/zh/use.html http://www.osyunwei.com/archives/9045.html http://bbs.linuxtone.org/thread-10110-1-1.html
